🎯 The essentials in 30 seconds
- Les MPA Best Practices v5.3 (Netflix, Disney, Warner Bros., etc.) recommend explicitly browser isolation and pixel streaming to protect sensitive content
- VirtualBrowser answers natively to critical controls TS-2.8 (internet access) and TS-2.9 (remote access)
- Express deployment : 2 minutes in SaaS, 2 hours in on-premise
- Optimized TCO : fraction of the cost of a traditional VDI solution
- Compliance “by design” : pixel streaming architecture aligned with MPA recommendations
La Motion Picture Association (MPA), through its program Trusted Partner Network (RPM), published the MPA Content Security Best Practices v5.3.1 that set the safety standard for the media and entertainment industry.
These best practices reflect the expectations of major studios - Netflix, Paramount, Paramount, Amazon Studios, Sony, Universal, Walt Disney, and Warner Bros. - and are becoming a contractual prerequisites for VFX, post-production, and digital production service providers.
The TS-2.8 (Internet Access) and TS-2.9 (Remote Access) controls explicitly recommend the use of Remote Browser Isolation and Pixel Streaming tools. This article details how VirtualBrowser meets these critical requirements.
Why MPA TPN compliance has become a must
The media and entertainment industry manages highly valuable content in a fragmented ecosystem: studios, VFX agencies, post-production, external consultants. This essential collaboration creates an extensive attack surface.
Main risks identified:
- Pre-release content leaks (scripts, rushes, preview versions)
- Exfiltration via unsecured remote access
- Phishing targeted at teams with access to sensitive content
- Unauthorized use for AI training (new in v5.3.1)
In fact, TPN certification has become a contractual requirement for working with major studios. Technical controls are particularly closely monitored during audits.
MPA TPN technical checks: how VirtualBrowser answers
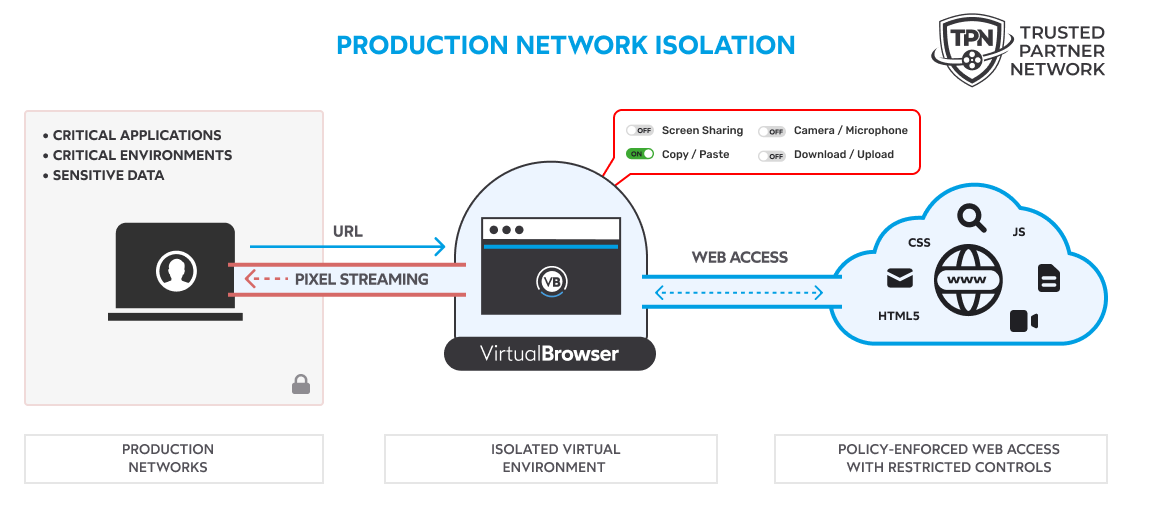
1. TS-2.8: Internet access from production networks
What MPA requires:Prohibit direct access to the Internet from production networks. If access is required, use an isolated virtual environment.
MPA explicit recommendation:
“For web browsing and email access, use browser isolation tools via a virtual environment separate from the production network.”
How VirtualBrowser responds:
- Each user session runs in a isolated virtual environment, physically separated from the production network
- The browser works entirely on the server side
- No web data is transmitted to the user computer (no HTML, JavaScript, files)
- Only an optimized video stream is broadcast (such as during a streaming (Netflix, Replay, etc.)
- The production network remains fully protected from the public Internet
✅ Full TS-2.8 compliance - Architecture aligned with MPA recommendations
2. TS-2.9: Secure remote access for consultants and contractors
What MPA requires: Secure remote access to production networks with strong encryption, copy and paste control, and identity verification.
MPA critical recommendation:
“Use pixel streaming applications to avoid transferring content to local systems.”
How VirtualBrowser responds:
- Technology Pixel Streaming native: the browser works on the server side, only the video stream is broadcast
- No web content uploaded on the remote user's computer
- Granular copy and paste control (activable/deactivable by policy)
- Strong authentication (SSO/SAML/LDAP)
- Extensive logs for audit and traceability
Concrete example: A VFX consultant in London accesses SaaS tools and creative references without ever touching the studio's production network, and without transferring content to his personal computer.
✅ Full TS-2.9 compliance - Pixel streaming explicitly recommended by the MPA
3. TS-2.5: Isolation of production networks
What MPA requires: Isolate production networks physically or logically from other networks (offices, Internet, DMZ).
How VirtualBrowser responds: VirtualBrowser acts like secure buffer zone between the Internet and the production network:
- Deployment in DMZ or dedicated network segment
- Browsing sessions never have direct access to the production network
- Precise control of accessible web resources
- Unidirectional flow (pixel streaming to the user only)
✅ TS-2.5 Direct Input - Network isolation architecture
4. TS-1.9 & TS-2.10: Email and web threat protection
What MPA requires:
- TS-1.9 : Filter emails to block phishing, malware, content exfiltration
- TS-2.10 : Filter the web against malicious and ransomware sites
How VirtualBrowser responds:
- Total insulation : webmail (Outlook 365, Gmail) and websites run in an isolated environment
- Zero-Day Protection : even unknown threats cannot compromise the user station
- Defense-In-Depth : even if a malicious link passes the filters, the execution remains confined
- The client only plays a video stream, never web code (HTML/Javascript)
✅ TS-1.9 & TS-2.10 multi-layer protection - Beyond traditional filtering
Summary: VirtualBrowser and MPA TPN compliance
Concrete use cases
Case 1: VFX artists accessing references online
Situation: 3D artists are working on a blockbuster and need visual references (Pinterest, ArtStation) from their workstation connected to the production network.
Problem: TS-2.8 prohibits direct access to the Internet from the production network.
VirtualBrowser Solution:
- Deployment in a dedicated DMZ (2 hours for on-premise, 2 min for SaaS)
- Access via your web browser (no agent to install)
- Isolated navigation with video feed only to the station
- Whitelisting possible on authorized sites (Pinterest, ArtStation, etc.)
✅ Result: TS-2.8 compliance + productivity maintained
Case 2: External consultants on a confidential project
Situation:External consultants (3-month mission) who need access to Shotgrid, Frame.io and Microsoft 365 from the studio.
Problem: TS-2.9 requires pixel streaming to avoid transferring content to personal computers.
VirtualBrowser Solution:
- 2-minute provisioning + SSO/SAML authentication
- Access to SaaS tools via pixel streaming
- Copy and paste control (can be disabled)
- Extensive audit logs
✅ Result: TS-2.9 compliance + instant onboarding + full traceability
Why VirtualBrowser for MPA TPN compliance
Compliance “by design”
The pixel streaming and physical isolation architecture answers natively to MPA TS-2.8 and TS-2.9 recommendations. No complex configuration.
TPN certification made easy
During audits, easily demonstrate:
- Separate virtual environment for web browsing (TS-2.8) ✅
- Pixel streaming for remote access (TS-2.9) ✅
- Isolation of production networks (TS-2.5) ✅
- Logs and traceability of sessions ✅
Express deployment, optimized TCO
- On-premise : 2 hours
- SaaS : 2 minutes
- No agent : access via standard web browser
- TCO : fraction of the VDI/Citrix cost for equivalent or even better security
Seamless user experience
Optimized video streaming with no noticeable lag. Users navigate naturally, without noticing the underlying isolation.
Maximum IP protection
VirtualBrowser uses the Pure pixel streaming :
- No HTML/Javascript data goes across the network
- Maximum protection against intellectual property exfiltration
- Strict compliance with MPA TS-2.9 recommendation
VirtualBrowser: 15 years of expertise in the protection of sensitive content
100,000+ active users in highly secure environments: defense (Naval Group, Thales), critical infrastructures, banking sector. The media and entertainment industry is a natural use case for our technology.
Sovereignty and compliance:
- France default hosting
- Native GDPR compliance
- On-premise option for total control
- European digital sovereignty
Conclusion
MPA Best Practices v5.3 are explicit: to secure Internet access from production networks (TS-2.8) and remote access (TS-2.9), studios need to deploy browser isolation tools and pixel streaming.
VirtualBrowser natively meets these requirements:
- Remote Browser Isolation with full physical isolation
- Pixel streaming (no DOM reconstruction)
- Express deployment (2 min SaaS, 2 hours on-premise)
- Seamless user experience
- Optimized TCO vs VDI/Citrix
For studios, VFX agencies, and post-production houses, VirtualBrowser is a TPN compliance accelerator while maintaining the productivity of creative teams.
resources
📚 MPA TPN documentation
MPA Content Security Best Practices v5.0 - Objectives & Methodology
Official MPA guide detailing technical controls and recommendations (including TS-2.8 and TS-2.9).
🎯 Request a demo
Our experts show you in 15 minutes how VirtualBrowser, a solution for Remote Browser Isolation for the protection of sensitive content, meets the TPN technical controls in your environment. Request your demo here


